TYPES OF COMMUNICATION DEVICE
A communication device is a hardware device capable of transmitting an analog or digital signal over the telephone, other communication wire, or wirelessly. The best example of a communication device is a computer Modem, which is capable of sending and receiving a signal to allow computers to talk to other computers over the telephone. Other examples of communication devices include a network interface card (NIC), Wi-Fi devices, and an access point.
A communications device that can convert digital signals to analog signals and analog signals to digital signals, so that data can travel along an analog telephone line.
- Digital Modem (ISDN,DSL,Cable Modem)
A communications device that sends and receives data and information to and from a digital line.
Some mobile users have a wireless modem that uses the cell phone network to connect to the Internet wirelessly from a notebook computer, a smart phone, or other mobile device.
Next Card
Sometimes called a network interface card, is a communications device that enables a computer or device that does not have built-in networking capability to access a network.
Wireless Access Point
A central communications device that allows computers and devices to transfer data wirelessly among themselves or to transfer data wirelessly to a wired network .
*Wireless access points have high-quality antennas for optimal signals.
Router
A communications device that connects multiple computers or other routers together and transmits data to its correct destination on a network.
Switch
A connection device similar to a hub but more sophisticated, including functionality that allows it to control and manage data transmissions.
Hub
A connection device that allows multiple connections to the network.
TYPES OF TRANSMISSION MEDIA
Transmission media is a pathway that carries the information from sender to receiver. We use different types of cables or waves to transmit data. Data is transmitted normally through electrical or electromagnetic signals.
An electrical signal is in the form of current. An electromagnetic signal is series of electromagnetic energy pulses at various frequencies. These signals can be transmitted through copper wires, optical fibers, atmosphere, water and vacuum Different Medias have different properties like bandwidth, delay, cost and ease of installation and maintenance. Transmission media is also called Communication channel.
(1) Wired or Guided Media or Bound Transmission Media : Bound transmission media are the cables that are tangible or have physical existence and are limited by the physical geography. Popular bound transmission media in use are twisted pair cable, co-axial cable and fiber optical cable. Each of them has its own characteristics like transmission speed, effect of noise, physical appearance, cost etc.
Twisted Pair Cable
•Twisted-pair cable consists of one or more twisted-pair wires bundled together.
•Widely used transmission media for network cabling and telephone systems.
Coaxial Cable
Consists of a single copper wire surrounded by at least three layers:
An insulating material
A woven or braided metal
A plastic outer coating .
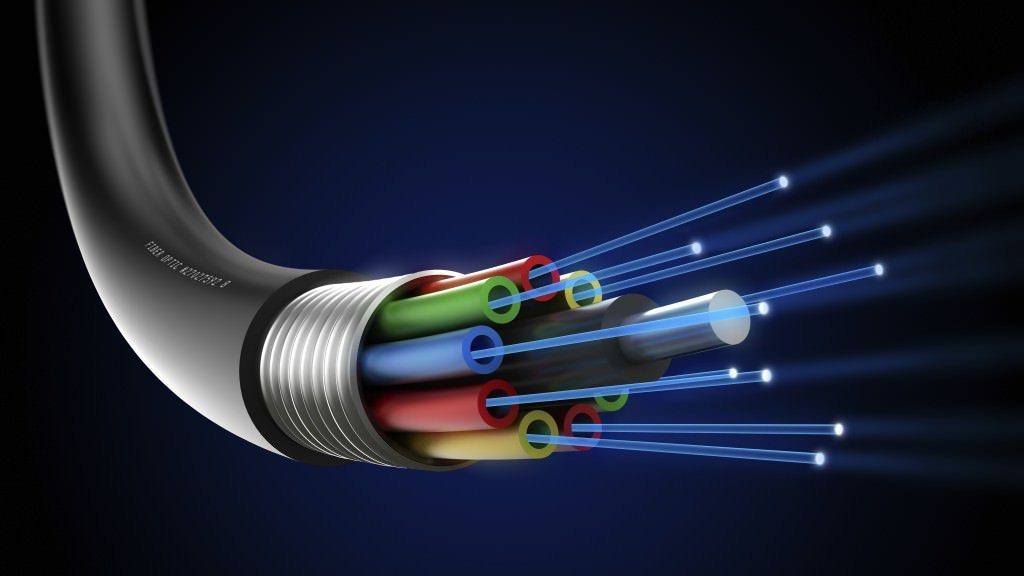
Fiber Optic
A transmission media that uses glass or plastic fiber to carry light (laser) signals.
(2) Wireless or Unguided Media or Unbound Transmission Media : Unbound transmission media are the ways of transmitting data without using any cables. These media are not bounded by physical geography. This type of transmission is called Wireless communication. Nowadays wireless communication is becoming popular. Wireless LANs are being installed in office and college campuses. This transmission uses Microwave, Radio wave, Infra red are some of popular unbound transmission media.
Infrared
Infrared (IR) is a wireless transmission medium that sends signals using infrared light waves.
Broadcast Radio (Bluetooth, Ultra Wideband (UWB), WiFi, WiMAX)
A wireless transmission medium that distributes radio signals through the air over long distances such as between cities, regions, and countries and short distances such as within an office or home.
Cellular Radio (2G,3G,4G)
A form of broadcast radio that is used widely for mobile communications, specifically wireless modems and cell phones
Microwave
Microwaves are radio waves that provide a high-speed signal transmission.
* Microwave transmission, often called fixed wireless, involves sending signals from one microwave station to another.
Communications Satellite
Is a space station that receives microwave signals from an earth-based station, amplifies (strengthens) the signals, and broadcasts the signals back over a wide area to any number of earth-based stations.









/cdn.vox-cdn.com/assets/1153853/external-dialup-modem-back-panel.jpeg)





/162249-SG300-28P-56a6f9835f9b58b7d0e5c9fd.jpg)






/trademarkregistered-598a056768e1a200116dc33a.jpg)